
Pradeep Kumar Madasu
January 06, 2025Cybersecurity in the Digital Age: Protecting Your Business from Evolving Threats
The entire world is coming online. Business communications trading everything is now on a server and can be remotely accessed.
With this rapid shift, businesses are vulnerable to cybersecurity threats. According to a report by Statista, more than 880 thousand people reported cybercrime only in the U.S.
This leaves us with the question of how safe our business is.
Cloud storage attacks and supply chain attacks are the most common and most harmful, as well.
You can read more about it in Statista’s report.
The Importance of Cybersecurity
Cybersecurity includes a range of practices and technologies designed to protect networks and businesses from malpractices and harmful actions.
Cybersecurity practices are growing and adapting to the increase in cyber threats and crimes.
Cybersecurity is a growing industry, as evidenced by this report from Statista.
The report clearly reflects the projection of revenue from US$ 167.3 billion to US$ 271.9 billion by 2029.
The consequences of inadequate cybersecurity can be severe.
Data breaches can lead to significant financial losses, reputational damage, and legal repercussions.
For example, the damage done by cybercrimes in the U.S. alone was 12.7 billion dollars, which is a 21% increase from 2023.
Additionally, businesses that experience a breach often suffer from problems like loss of customer trust and increased observation from government bodies as well.
Evolving Cyber Threats
As technology evolves, so do the tactics used by cybercriminals. Some of the most prevalent threats include:
- Ransomware: This is malicious software that will lock your system down with a safety protocol. These kinds of software can also lock you out of your own laptop or devices or encrypt your data files. Then, in order to use them again, you have to pay ransom to the person operating this software. According to Sophos, the average ransom collected through these kinds of attacks was $2.73 million in 2024.
- Phishing: Phishing is when you are being tricked into revealing your sensitive information like social security number and credit card details, and in the case of business, it can be passwords, emails, and even access logins. According to a report on Phishing, close to one million people fell victim to this only in the first quarter of 2024.
- Distributed Denial-of-Service (DDoS) Attacks: These attacks overwhelm a network or service with traffic, rendering it unavailable to users. DDoS attacks are harmful for businesses, though they are not a security breach, but while this is into play, a lot of other malicious activities can occur on your website or servers. Last year, Cloudflare mitigated the largest DDoS attack, reaching up to 5.6 terabits(Tbps) per second and 666 million packets per second. The attack lasted for 80 seconds. In these 80 seconds a lot of damage was already done.
- Insider Threats: Employees who access sensitive information can pose significant risks, whether intentionally or unintentionally. Gurucul did a report in which they stated that 48% of organisations have reported more insider threats in the last 12 months. Not only this, but 83% of organisations have reported at least one insider attack.
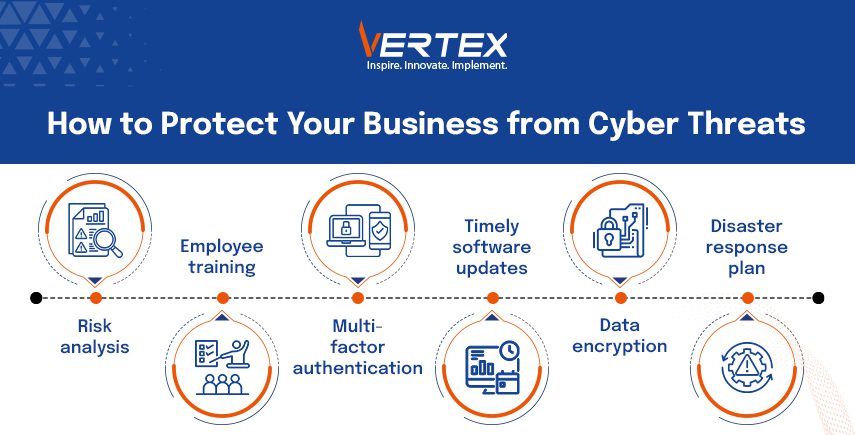
Prevention Measures for Cyber Threats
We have already covered how cybercrime is at an all-time high, and so are different types of online threats.
To safeguard your organisations and businesses, you must take some extra steps. Some of them are mentioned below
1. Analyzing Potential Threats
- The first prevention measure you can take is to make sure you analyse your system security at regular intervals. Doing this will ensure proper functioning, and you can also isolate any vulnerability that you may find.
- You must evaluate risks based on impact and likelihood to minimise cybersecurity threats. Through this, we can very easily calculate the risks. The formula works like Risks = Impact x Likelihood.
- Once the risks are evaluated, we can decide how many resources we need to tend to a high risk compared to a low risk.
2. Employees Awareness Towards Cyber Threats
- Organisations must invoke training of employees to make them aware of different types of cybercrimes. They should also be given training as to how to identify and response if such a situation is upon them.
- Do mock phishing drills and DDoS attack drills so that employees or organisation members know the protocols to take during such a situation.
3. Multi-Factor Authentication (MFA)
- Multiple forms of verification are required before granting access to sensitive systems. Biometrics and vocal authentication work best in these cases.
- MFA significantly reduces the risk of unauthorised access. This will also significantly reduce the insider threat by a large margin.
4. Timely Software Updation
- Ensure that all software and systems are up-to-date with the latest security patches. Never go for pirated versions of software.
- Cyber crimes mostly occur in organisations with outdated software and security software.
5. Data Encryption
- Encrypting the data is one of the most well-known methods of keeping your data and sensitive information safe. This adds an extra layer of security to your data
- Different levels of encryption should be used to make sure a pattern is not formed. Making it harder to decode.
6. Disaster Response Plan
- Develop and regularly update a protocol or SOP outlining steps to take in the event of an attack. This will result in swift action without any confusion.
- Conduct drills to ensure that employees know their roles during an incident.
AI and Machine Language in Cyber Security
Artificial intelligence and machine learning have both been utilised by many organisations to analyze a large amount of data and to recognise any patterns, anomalies, or vulnerabilities.
Many organisations have already adapted and incorporated these two in their process to prevent cyber security threats.
According to a report by MarketsandMarkets, the AI market in cybersecurity is estimated to reach $60.6 Billion by 2028.
With more and more companies moving to the cloud, security threats are increasing daily.
A survey by McAfee found that 83% of organisations experienced at least one cloud-related security incident in 2020.
This number is increasing rapidly, and similarly, cloud security methods are also getting updated so that they are ready for any threats.
According to a report by Statista, the annual revenue of 2024 for cloud security is 2 billion USD.
Compliance and Regulations
When running a business, it is necessary to abide by the laws put forward by the government and comply with them.
When we talk about data, not only national but international laws also come into play.
Bodies like CCPA ( California Consumer Privacy Act) and GDPR (General Data Protection Regulation.
These are in place so that no misuse of data is conducted.
Organisations must follow these simple steps to be compliant with these regulations.
- Have proper information on the code of ethics and cyber crime regulations that are being applied to your organisation, and keep track of any amendments that are made to these regulations.
- Implement policies that align with legal requirements regarding data protection.
- Controlled audits should be done at regular intervals to make sure things are running smoothly.
Conclusion
Wrapping up organisations should learn and adapt to the ever-evolving cyber threats.
By understanding the threats and implementing methods that include technology, training, and compliance, organizations can prevent any cyber threats from coming their way.
Now, investing in cyber security is not only an option but a necessity.
If any organisation fails to do so they are putting their company data and even stakeholders at risk.
This article provides an overview of the critical aspects of cybersecurity relevant for businesses today while emphasizing the importance of preventive measures against evolving threats.
Recent Blogs
19 May, 2025

19 May, 2025
12 May, 2025

5 May, 2025

28 April, 2025

21 April, 2025

14 April, 2025

7 April, 2025
Recent News

2 February, 2025

14 November, 2024

4 November, 2024

1 August, 2024

6 March, 2024

28 February, 2024

12 June, 2023



